A new phishing campaign is making the rounds, essentially preying on trust and specifically targeting website owners who use WooCommerce—a popular eCommerce plugin for the WordPress content management system.
WooCommerce powers millions of online stores around the world and helps businesses of all sizes manage product listings, process payments, handle shipping, and more, all within the familiar WordPress dashboard.
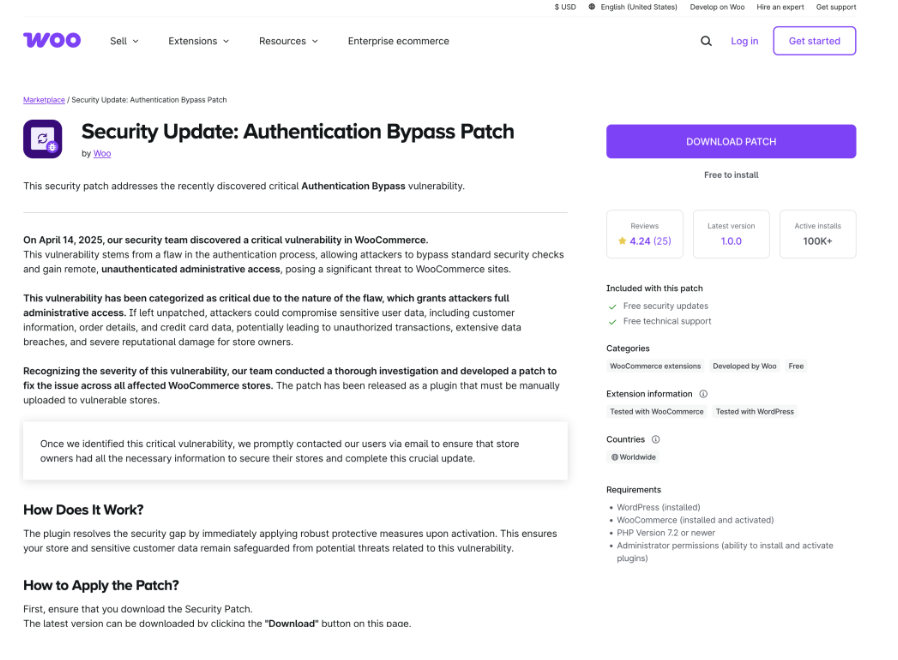
Researchers at Pathmark have been monitoring and analyzing the detection. They’ve found fake emails are being sent out that appear to come from WooCommerce, warning users about a fake vulnerability and urging them to install a critical patch. But this so-called “patch” is actually disguised as malware to give attackers full control over your online website and store.
The phishing email warns of a fictional vulnerability called “Unauthenticated Administrative Access” and prompts users to download a patch to secure their site. The email and website are crafted to look like official WooCommerce communications. In fact, the fake website even uses a visually deceptive domain name—woocommėrce[.]com—where a special character replaces the letter “e.” This is a classic HTTP spoofing (or an IDN homograph attack), used to fool even cautious users by replacing a single character or number with an alternative, usually a unicode symbolled letter.
Possible Effects
Clicking the link takes victims to a fake WooCommerce Marketplace page where they’re prompted to download a ZIP file and install it as a plugin. Instead of patching anything, the plugin quietly:
- Creates a hidden admin account, giving the attacker access to your website
- Sends site and user details to an attacker-controlled server
- Downloads additional malicious files (known as web shells), which allow remote control of the server
- Disguises itself from the WordPress admin panel to further avoid detection
Once this malicious plugin is installed, your website is no longer under your full control. Attackers can inject spam or scams into your pages, redirect your customers to shady websites, or even lock up your site and demand a ransom. They may also use your server to host malware and potentially attack others, putting your domain, website and reputation at risk.
Signs of Compromise
Some signs of compromise include a random username with 8 characters, an unknown cronjob, a folder in wp-content/plugins named “authbypass-update” or a folder in wp-content/uploads called “wp-cached-(random 8 character code).” If you do notice any of these, deleting them may not be enough. Reach out to your web host or a security expert to have your website scanned for any possible malware.
These attacks are designed to look legitimate, making them especially dangerous for both experienced developers and non-technical site owners, so its crucial to keep a vigilant eye out especially related to important services and integrations
How to Stay Safe
If you use WooCommerce or manage WordPress sites, remember:
- WooCommerce and WordPress never ask you to manually download and install patches via email. All official updates are delivered through the WordPress dashboard and their official websites.
- Be suspicious of emails warning about urgent security issues—especially if they include links or attachments.
- Always double-check sender addresses and inspect links (either hovering with mouse, or long-pressing with smartphone) before clicking. A minor character change in a domain name can be hard to spot but can make a huge difference in redirecting you to a website owned by an unrelated entity.
If you ever get an email and are doubt, go directly to the official website or your dashboard to verify any updates. If you do end up clicking on a click and/or inputting personal information, contact the company directly to report and make needed security changes such as to your password.
Phishing attacks continue to become increasingly commonplace and sophisticated, blending technical manipulation with psychological pressure. Whether you’re a casual tech user, student, developer or a small business owner running your own shop, staying vigilant is key in today’s technological landscape.
Always verify before you trust—especially when it comes to links, plugins, or urgent security messages. When in doubt, consult official sources or your hosting provider before taking action.


Leave a Reply