Author: Modernizing Tech
-
Amazon Extends Alexa+ AI Assistant With Website Access
Amazon’s Alexa+ AI assistant is getting expanded access with the new rollout of Alexa.com, a new web-based platform designed to let people interact with Alexa directly through a browser. The launch extends Alexa beyond smart speakers and smartphones, making it available across voice, mobile, and now desktop environments. The web experience is currently rolling out
-
HP Unveils Keyboard-Based AI PC and Neo:LED 4K Monitor
HP announced two major additions to its commercial lineup at CES 2026, introducing the HP EliteBoard G1a Next Gen AI PC, which places a full AI-capable computer inside a keyboard, and the HP Series 7 Pro 4K Monitor, designed for professionals who need high color accuracy and advanced display performance. HP says both products aim
-
NVIDIA Rubin Platform Announced as Rack-Scale Architecture for Large AI Systems
The Rubin platform has been formally announced as a rack-scale computing architecture aimed at powering large AI models, advanced reasoning systems and long-context inference workloads. Developed by NVIDIA, Rubin is designed as a coordinated platform rather than a standalone chip release, combining new GPUs, CPUs, networking technology, storage acceleration and security capabilities into a unified
-
Apple Announces New Fitness+ Programs and Research Highlighting Apple Watch Exercise Trends
Apple has announced a series of updates to Apple Fitness+ alongside new health research insights, reinforcing the company’s continued push into technology-driven wellness and activity tracking. Apple shared new findings from the Apple Heart and Movement Study, analyzing anonymized data from approximately 100,000 participants over four years. The results suggest Apple Watch users tend to
-
Plant-Based Thermal Paper Shows Real Promise as a Safer Alternative to BPA and BPS
Thermal paper remains deeply embedded in modern infrastructure, powering receipts, shipping labels, tickets, medical printouts, point-of-sale records and countless other transactions. Its convenience comes from chemistry: instead of ink, it uses a coating that reacts to heat to create text. For decades, that coating has relied heavily on bisphenol A (BPA) and bisphenol S (BPS)
-
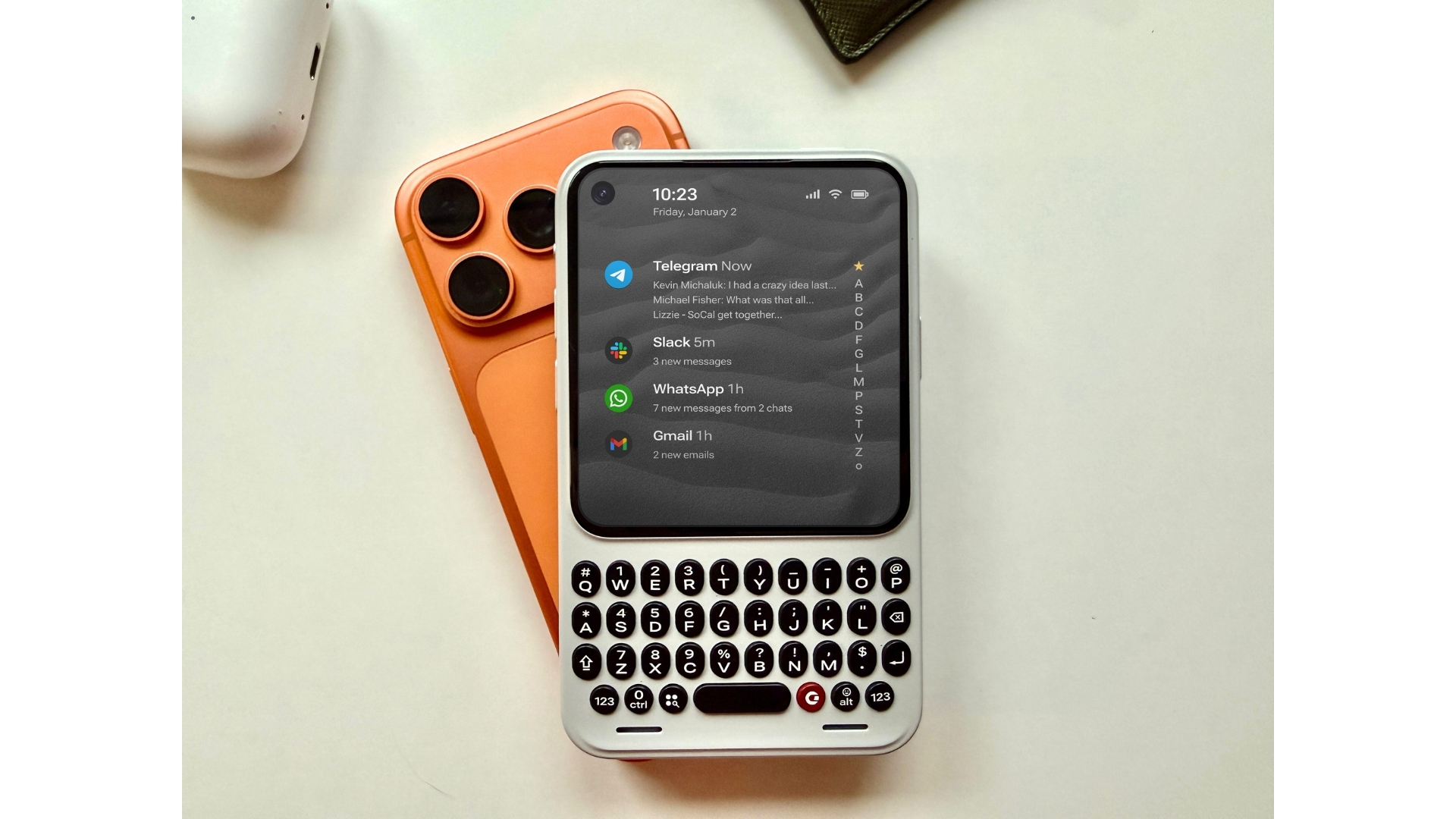
Clicks Communicator Tries to Bring Back Focus in a World of Distracting Smartphones
Clicks, the company that first gained attention for its physical Power Keyboard accessory designed to restore tactile typing to modern devices, is now planning something far more ambitious: its own standalone smartphone. While the Power Keyboard focuses on improving typing experiences across existing phones, tablets, televisions, and even AR/VR platforms, the company’s next step is
-
Malicious AI Chrome Extensions Steal ChatGPT and DeepSeek Conversations
Security researchers at cybersecurity softare company OX Security have uncovered a widespread malware campaign involving two Chrome extensions that impersonate a legitimate AI sidebar tool while covertly collecting users’ ChatGPT and DeepSeek conversations along with extensive browsing data. Combined, the malicious extensions have been installed by more than 900,000 users. Despite containing data-stealing functionality, one
-
Samsung Introduces Freestyle Plus Portable AI Projector Ahead Of CES 2026
Samsung has just announced a new portable projector, the Freestyle Plus, designed to bring smarter visuals and flexible entertainment to everyday spaces. The reveal comes just before CES 2026, the world’s largest annual consumer technology showcase held in Las Vegas, where companies debut upcoming innovations and products. The Freestyle Plus is built around artificial intelligence
Categories:
Have any comments or suggestions? Feel free to let us know!

